Yearn Finance has published a detailed post-mortem on last week’s yETH exploit, explaining how a numerical flaw in one of its older stableswap pools let an attacker mint an almost unlimited amount of LP tokens and steal about $9M in assets.
The DeFi platform said it has already recovered part of the stolen funds.
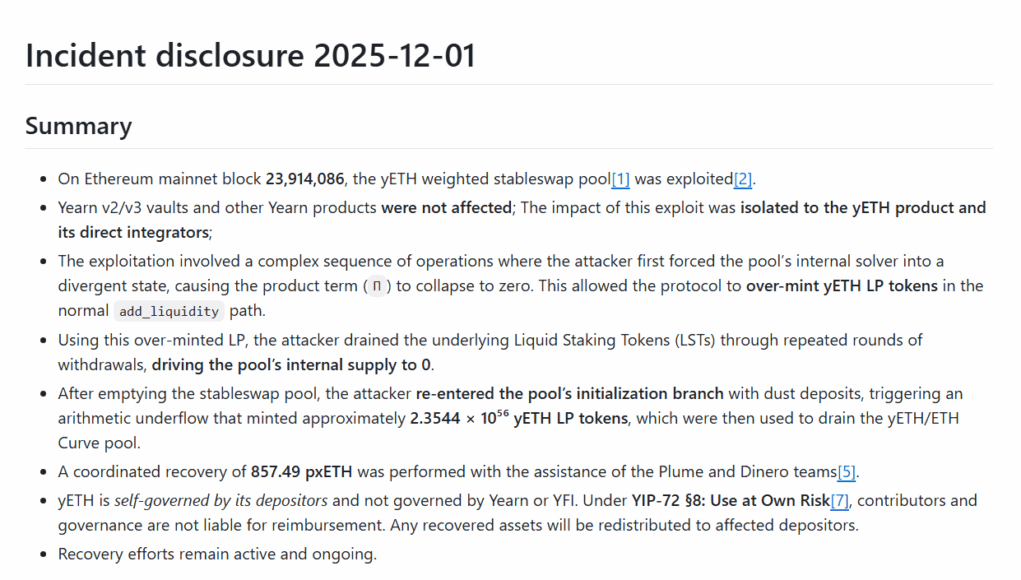
In the report, Yearn said the attack hit the yETH weighted stableswap pool at block 23,914,086 on November 30, 2025.
DISCOVER: Top 20 Crypto to Buy in 2025
Which Yearn Products Were Affected and Which Stayed Safe?
The breach followed what the team described as “a complex sequence of operations” that pushed the pool’s internal solver into a divergent state and then triggered an arithmetic underflow.
Yearn noted that its v2 and v3 vaults, along with the rest of its products, “were not affected.” The impact stayed limited to yETH and the systems tied to it.
The attacker targeted a custom stableswap pool that held several liquid staking tokens: apxETH, sfrxETH, wstETH, cbETH, rETH, ETHx, mETH, and wOETH, as well as a yETH/WETH Curve pool.
According to Yearn’s asset snapshot, the pools held a mix of LSTs and 298.35 WETH before the exploit occurred.
Yearn’s post-mortem breaks the attack into three clear steps.
In the first stage, the attacker used a series of imbalanced add_liquidity deposits that pushed the pool’s fixed-point solver into a state it wasn’t built to manage.
That move caused the internal product term, Π, to fall to zero. Once that happened, the weighted-stableswap invariant failed, allowing the attacker to mint far more yETH LP tokens than the value they had actually deposited.
With those inflated LP tokens in hand, the attacker moved to the next phase.
They repeatedly called remove_liquidity and related functions, pulling out almost all of the LST liquidity. Most of the loss shifted onto protocol-owned liquidity inside the staking contract.
DISCOVER: 9+ Best High-Risk, High-Reward Crypto to Buy in 2025
What Funds Has Yearn Recovered So Far, And Who Will Receive Them?
According to Yearn, this sequence drove the pool’s internal supply to zero even though ERC-20 balances still showed tokens in the contract.
In the final step, the attacker slipped into a “bootstrap” initialization path that was only intended for the pool’s first launch.
By sending a crafted dust-level configuration that broke a key domain rule, they triggered an unsafe subtraction. That underflow created a massive batch of new yETH LP tokens and completed the exploit.
Yearn said the underflow was so severe that it created what the team called an “infinite-mint.” The attacker used this flaw to drain the yETH/ETH Curve pool.
The project said it has recovered 857.49 pxETH so far with help from the Plume and Dinero teams. A recovery transaction took place on Dec. 1.
Yearn plans to return the recovered assets to yETH depositors on a pro-rata basis, using balances from right before the exploit. Any further recoveries, whether from cooperation by the attacker or from new tracing efforts, will also go to depositors. The timeline released by Yearn shows that a war room was formed about 20 minutes after the breach.
The SEAL 911 response group joined soon after. Investigators say the attacker sent 1,000 ETH to Tornado Cash later that night, and moved the remaining funds through the mixer on Dec. 5.
Earlier reporting from The Block said roughly $3M in ETH moved through Tornado Cash in the hours after the attack.
The post-mortem also reminds users that YIP-72 governs yETH. It points to the product’s “Use at Own Risk” clause, which states that Yearn contributors and YFI governance are not responsible for covering losses.
The report says any recovered funds will go back to affected users.
DISCOVER: 15+ Upcoming Coinbase Listings to Watch in 2025
The post Everything You Need to Know About Yearn Finance Exploit appeared first on 99Bitcoins.